Another kind of MAC
Edward Lancaster
19th December 2013
With most of us living our lives online via the phone in our pocket, no longer is it a private life but a very public one. The distinction between what is our private space and the public domain has become disputed ground. Our private lives that were once confined to our immediate physical space, whether that was the home or a chat amongst friends in a bar, have now extended. Our private spaces now overlap and are shared with others online[1], our chats with friends exist across the globe and back again, online content penetrates our home, where many of us transmit our own content back out again.
It is unsurprising that our wireless lives and the data we transmit would not go unnoticed, however it is also unsurprising that the collecting of this data has often acquired Orwellian connotations. Whether this is due to the predominantly dystopian approach to sci-fi becoming so ingrained within our paradoxical attitude to technology, or the media’s preference for perpetuating a sense of anxiety – or possibly it may just be a healthy dose of scepticism. Whatever the reason, the notion of our data being taken is uncomfortable. There is no shortage of stories of illicit data mining, from Google earth’s cars illegally storing wifi data from every house it passes, to recycling bins in London that track passers by. This need not be the case, from major projects that hope to mine big data to predict natural, economic or man made disasters, to small scale design research that aims to integrate our wireless selves into our architecture, creating a more adaptable and smarter urban planning. There is great potential for our phones to be used to better integrate and experience the physical world so as to bridge the two worlds we inhabit: digital and real. One such piece of data that has the potential to do this is the unique wifi address, called the MAC address that is transmitted from every Smartphone. From the initial awareness and research that went into a previous blog post on Renew’s Bins, it was decided to investigate MAC addresses further to investigate other design potentials beyond a listening bin. The MAC address seemed the perfect starting point for experimenting with other uses of data rather than targeted advertising.
What is a MAC address?
An anagram of ‘Media Access Control’ every wifi-enabled phone has within it a 48-bit, 12 digit number consisting of 6 groups of hexidecimal digits separated by a colon (see fig 1). It is a number you would not know unless you looked for it, as it is part of the devices automated processes that enable a smoother operation of the applications you participate in. It is the communication that happens on a sub layer, as you are not the only person who speaks on your phone, your phone also speaks. It talks frequently, possibly more than you. It speaks to as many wifi access points that are willing to speak to it, sending probing packets of data to enquire as to whether the wifi access points are known to it or not, so as to connect to a possibly faster network (rather than 3G).
The MAC address is the international standard of LAN and WLAN communication set by the Institute of Electrical and Electronic Engineers (IEEE). First implemented as part of Xerox Park’s Ethernet scheme, it has become the standard of all WLAN (wifi is the synonym) technology. As such this small often unnoticed group of numbers surrounds every inhabited space (on the condition that the inhabitant has a smart phone).

Applications
As a means of obtaining highly personalised data, MAC addresses share little. They can tell you the phone you own (This has been used to obtain statistical data on the market share of Smartphone manufacturers). They can be used to count people or cars, they can be used to track shoppers within a retail store to determine their (approximate) movement, or as the controversial Renew bins in London tried to do, track movement over time and within a specific location (the financial district). The purpose of which was to attempt to amass a unique pattern for each phone (and of course its owner). This particular project and how it works (and a better understanding of MAC addresses) was covered by Tom Taylor at Scrap lab.
As the Woody Allen gag goes “80% of success is showing up” and that’s what the MAC address can tell you, who is here. That was the starting point of the research we undertook. What interesting interactions and experiences can be gained from simply knowing that someone is here?
Development
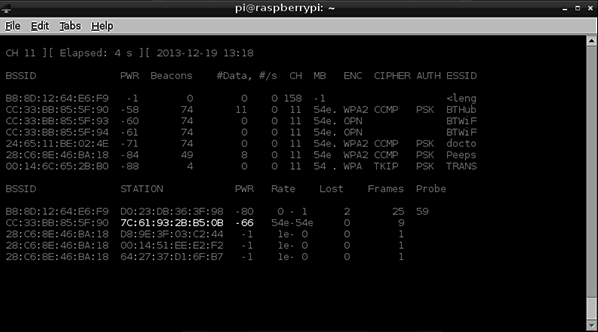
To explore the possibilities of handling MAC addresses as a source of data, we set out to build a simple double function program. The two ambitions were simple: to check who is present and then cross-reference those present with previous scans. The first task was to obtain the MAC addresses. Starting simply with a Raspberry Pi and a wifi interface we used a piece of software called Aircrack-ng and its subprogram Airodump-ng (see fig 2) to scan for MAC addresses[2] (there are other programs such as Kismet). Once we had access to all the available MAC addresses, it was time to take these anonymous numbers and turn the data into a more personalised experience.

Within the studio, everyone’s MAC address was assigned the name of the owner in the dictionary function of Python. Python then extracted the MAC addresses from Airodump-ng’s csv file. Iterating through the csv file of the MAC addresses that where found in the scan, these were cross-referenced with the dictionary of known MAC addresses and their owners (see code extract)[3]. The result was the ability to record the combinations of people that were present (Fig 3).
(code extract)
def check_address():
with open(‘/home/pi/MAC/address.csv’, ‘r‘) as f:
address=csv.reader(f, delimiter=‘,’)
for row in address:
for field in row:
for address in MAC.keys():
if address == field and address in MAC:
person = MAC[address]
combo_1.append(person)
f.close()##THE DICTIONARY OF KNOWN MAC ADDRESS AND THIER OWNERS
MAC = {’04:A8:xx:xx:B1:91′ : ‘Ed’, ’00:88:xx:xx:1A:F9′ : ‘Sam’, ‘F0:D1:xx:xx:D9:1E’ : ‘Ben’,
‘9C:04:xx:xx:73:96’ : ‘Paul’, ’54:26:xx:xx:F0:1C’ : ‘El’}

Of course, within a small studio, knowing that you are sat with the same people as before is no great revelation, but extrapolate that to a public place. Have you ever wondered how many people you have passed before on your local high street? Think of a time that you have encountered someone whose history has overlapped with your own, perhaps at the same university, or maybe you grew up in the same town. The potential of a design intervention that will illustrate the entwined nature of public space could only help illustrate the fact that we are not only connected wirelessly but remain physically connected on a very different local area network.
Initial observation
The initial problem of placing the scanner within the space of the studio is that the wifi of everyone’s phone connects directly to the studios wifi, and dependent on the phone and its power management (it takes energy to go looking for networks) the frequency at which it probes other networks is greatly reduced. This resulted in a low yield of known phones (and their owners).
What also came out of working with Airodump-ng was that not only does it report the MAC addresses that are present but also the power of each signal (see Fig 2). Although not accurate enough pinpoint the phone in space – even with additional scanners to triangulate the signal – the power reading can be utilised to distinguish between groups of people. The problem of locating people in space maybe more effective in an outdoor space without the interference of walls.
Physical output
In response to the criticism that the Renew recycling bins received (and their eventual suspension) the chief executive tried to dampen peoples fears by describing them as “glorified people counters” – this is not how they are described to potential advertisers on their website. However, this is another possibility of MAC code scanning, to retain the anonymity of the owner and simply reduce the phone to an entity to be counted.

This initial research had the intention of not prescribing outcomes but exploring the unique traces of data emitted from phones and exploring how they can be experienced – and what there is to be experienced – through design. So it was not only individualised relationships that were explored but also looking at the data-set as a mass. To do so we took the number of MAC addresses that where found and simply reduced them to a total number, this number was then mapped to the speed of a motor which in turn was attached to a piece of chalk; the greater the number of phones the faster the motor ran, creating a specific pattern distinguishable from lesser numbers (Fig 6). The physical output of an ever changing action begins to explore ideas around the patterns that are created or can be recorded from our transmitting pockets. A project that specifically uses MAC address data to dynamic effect is Selena Savic’ Quadricore. The project creates a dynamic architecture that utilises the MAC address scanner as a sensor for adjusting the physical space of its Smartphone carrying inhabitants.

Dynamically mapping or visually representing our wireless world, although not utilising the power of individual experiences, can result in interesting and engaging results. The light paintings of Timo Arnall are a great example of this. Visually representing the wavelengths that go into making our urban environment while saying nothing of each personal input, it speaks to everyone because it is built, used or at least inhabited by everyone. This is where Timo’s research is positioned, not engaging the data on an individual base, as a set of personal data, but looking at it as an urban material (or immaterial as he calls it). In his Wifi light paintings he uses long exposure photography to visualise the invisible. The photographs transform radio wavelengths to lights waves, illuminating (quite literally) the wireless networks that surprisingly don’t always surround us.

The interesting distinction between Timo’s projects and projects working with specific individuals data, is that of the ethical implications. Working with the wifi spectrum as a whole speaks volumes of the invisible urban environment but once you start delving into what all this data is, once you start assigning it no longer to the mass but to the individual, it not only become a question of how do we use this in an engaging form, but how to apply it with ethical consideration and sensitivity.
The debates circling around private and public data, whether or not Smartphone technology is bringing us closer together, will continue. There is no shortage of apps that rightly or wrongly claim to be doing so. But what is unquestioned is that our world is becoming increasingly wireless, which must be incorporated into the world in which design and art engage with, as Adam Greenfield writes:
“The truly pressing need is for translators: people capable of opening these occult systems up, demystifying them, explaining their implications to the people whose neighborhoods and choices and very lives are increasingly conditioned by them.”
The passive uses of MAC addresses have an interesting potential for design, as they are not exclusive to phone or app, simply acting as a beacon of your presence, simply announcing ‘hello I’m here’.
[1] See: Mitchell, William J.: City of bits (1995), Me++ (2003): MIT Press
[2] We used a Realtek chip set, this is important as not all chipsets can be placed in monitor mode. For a list of compatible chipsets go to: http://www.aircrack-ng.org/doku.php?id=compatibility_drivers.
[3] note: python can not read Airodump in real-time only its recorded csv file once the specified scanning time has elapsed, we set it to 10 second scanning periods.
